Understanding 5-Eyes: Member Countries and 3 Strategies to Evade Surveillance
Learn about the 5-Eyes alliance and its member countries, along with three effective strategies to evade online surveillance. Ideal for those interested in privacy protection and enhancing security.
2024-05-120 minute readWeb
Share
Introduction: What is 5-Eyes?
5-Eyes is an international intelligence-sharing alliance composed of the United States, the United Kingdom, Canada, Australia, and New Zealand, all English-speaking countries. It operates primarily through a network known as Echelon, facilitating the exchange of information among member states. This collaboration began after World War II, initially focused on gathering intelligence on the Soviet Union and its allies during the Cold War, but has since evolved to address a wider range of threats.
This article provides an overview of 5-Eyes, its impact on individual privacy, and strategies to protect oneself from its surveillance.
History of 5-Eyes
The history of Five Eyes dates back to 1941 during World War II when the United States and the United Kingdom felt the need to share intelligence to counter common threats, leading to the BRUSA Agreement (Britain-United States of America agreement). This agreement enabled the sharing of information related to codebreaking and communications interception, later expanded to include Canada, Australia, and New Zealand, forming the present-day Five Eyes alliance.
Even after the collapse of the Soviet Union and the end of the Cold War, Five Eyes persisted, continuing its activities to address new threats, particularly terrorism, cyber threats, and foreign intelligence activities. These modern threats transcend borders and may impact civilian infrastructure and individual privacy. To counter these, Five Eyes engages in various initiatives, including information sharing and collaborative technological developments.
Similar Concepts: 9-Eyes, 14-Eyes, 41-Eyes, and 43-Eyes
Two well-known concepts similar to 5-Eyes are "9-Eyes" and "14-Eyes."
9-Eyes: This refers to an information-sharing agreement among the 5 Eyes countries plus Denmark, France, Norway, and the Netherlands. While similar to 5-Eyes, 9-Eyes is less widely recognized, potentially posing a blind spot for privacy-conscious individuals.
14-Eyes: Building on 9-Eyes, 14-Eyes includes Belgium, Germany, Italy, Spain, and Sweden. These countries share information similarly to 5-Eyes and 9-Eyes but on a broader scale.
Furthermore, there are more comprehensive concepts such as 41-Eyes and 43-Eyes.
- 41-Eyes: This refers to a network responsible for intelligence cooperation among allied forces in Afghanistan, connected to the United States-operated CENTRIXS-ISAF. It expanded to be known as 43-Eyes in 2010.
* The 41-Eyes includes countries such as Austria, Belgium, the Czech Republic, Denmark, Germany, Greece, Hungary, Iceland, Italy, Japan, Luxembourg, the Netherlands, Norway, Poland, Portugal, South Korea, Spain, Sweden, Switzerland, and Turkey.
All these alliances, including 5-Eyes, aim to gather intelligence, analyze threats, and enhance international security in response to various global challenges.
The Impact of 5-Eyes on Individual Internet Activities

5-Eyes is an international intelligence-sharing alliance comprising the United States, the United Kingdom, Canada, Australia, and New Zealand. Member countries of 5-Eyes have the capability to monitor and collect data from communications and activities conducted over the internet. This surveillance raises concerns about privacy infringement and the risk of personal information leakage. Additionally, 5-Eyes may request information and cooperation from technology companies, further raising concerns about privacy and data protection.
The framework of 5-Eyes is primarily led by the United States' NSA, known for its PRISM program designed to track individuals' online activities. PRISM involves the mass collection and surveillance of internet communications data, initiated in 2007 and primarily conducted in collaboration with major technology companies to collect and analyze data such as emails, chats, and video calls. The existence of PRISM came to light in 2013 when former NSA contractor Edward Snowden leaked classified information, sparking significant international debate.
Furthermore, speculation has arisen, particularly in countries like Japan, about the possibility of joining 5-Eyes from the perspective of their policies toward China and Russia, suggesting the potential for further expansion of this framework in the future.
In summary, 5-Eyes poses the potential to infringe upon individuals' privacy on the internet. Therefore, individuals concerned about privacy should take measures to protect themselves.
Strategies to Evade 5-Eyes Surveillance
To evade the surveillance network of 5-Eyes, using privacy-conscious online services is beneficial. Here are some methods, but it's important to combine several methods rather than relying on a single one.
Use of VPNs or Tor
The most straightforward way to conceal personal information is by connecting to the internet through a VPN.
A Virtual Private Network (VPN) encrypts internet communication, ensuring secure transmission. By using VPN client software to connect to a VPN server, your online activities and IP address are hidden as communication passes through the VPN server.
VPNs are commonly used not only for privacy protection but also for circumventing geoblocking. Here are some benefits of using VPNs:
- Privacy Protection: VPNs hide your online activities from internet service providers and observers. By communicating through a VPN, your IP address and online behavior are concealed from third parties.
- Enhanced Security: VPNs encrypt communication data, protecting against hacking and data theft, particularly on insecure networks like public Wi-Fi.
- Bypassing Geographical Restrictions: VPNs allow you to spoof your geographical location, enabling access to region-restricted content such as streaming services.
However, it's not advisable to use VPN services with servers or offices located in 5-Eyes member countries. Communications within 5-Eyes member countries are likely subject to censorship or surveillance.
Here is an article recommending VPN services suitable for 5-Eyes countermeasures. VPN services differ in terms of pricing and logging policies, so it's essential to compare them thoroughly.
While more challenging to set up, using Tor is preferable for ensuring higher security.
Using Disposable Email Addresses
Using disposable email addresses is not only useful for protecting one's identity but also for shielding oneself from spam. Many disposable email services deactivate addresses after about 10 minutes, making it difficult to track individuals even if the addresses were exposed to surveillance. Additionally, generating new phone numbers at any time can be advantageous when registering on websites where revealing personal information is undesirable.
In addition to disposable email addresses, it's recommended to use secure email services like ProtonMail or Tutanota. These services implement end-to-end encryption for email systems and enable mail viewing via the Onion Network, enhancing privacy. With end-to-end encryption, email content is encrypted between endpoints, preventing service operators from peeking into message contents.
Using Disposable Phone Numbers
One of the most significant risks to personal identification is the exposure of one's phone number. Since phone numbers are closely associated with individuals and not easily changed, casually registering one's own phone number on web services poses significant risks. To mitigate these risks, SMSOnline, which provides free disposable phone numbers to users worldwide, proves useful.
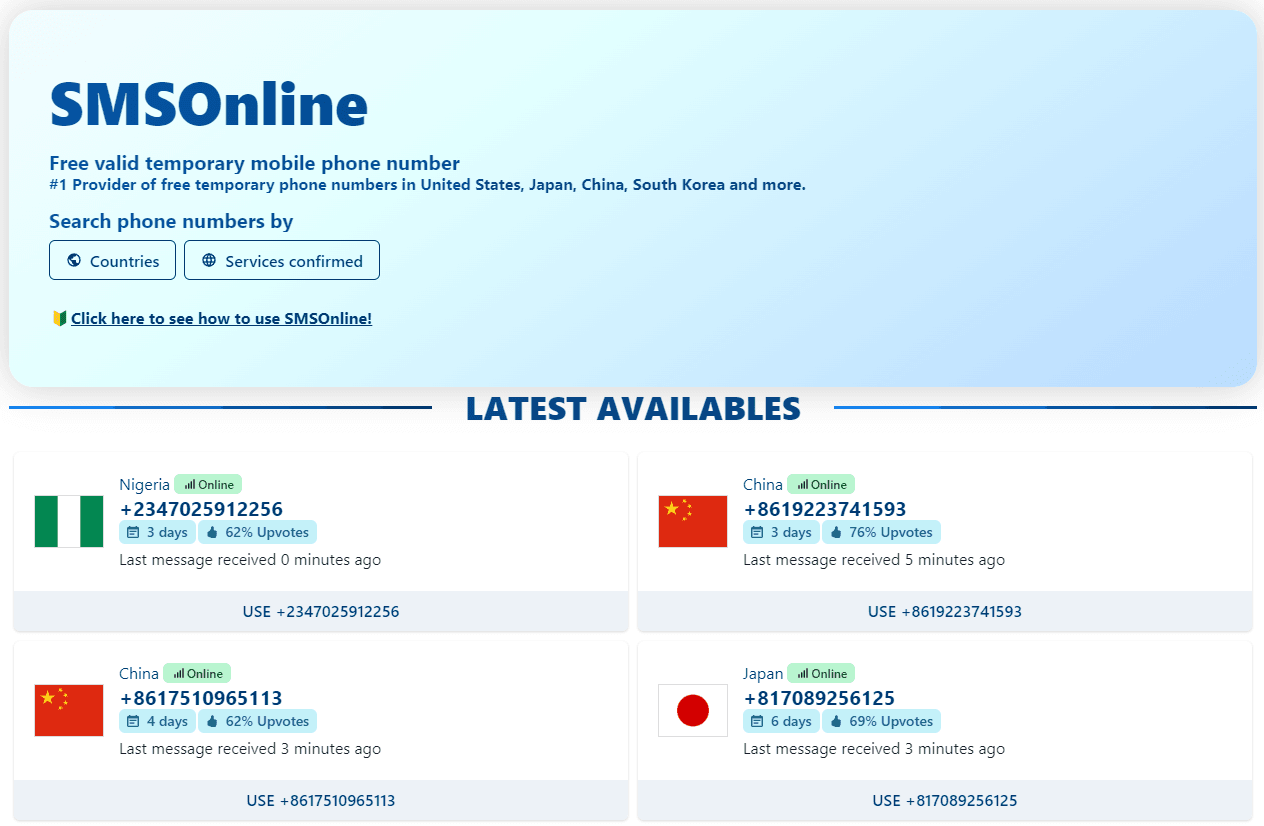
https://www.smsonline.cloud/
SMSOnline shares disposable phone numbers from various regions globally, allowing users to view SMS messages received on these numbers via the web. By using SMSOnline, individuals eliminate the need to expose their actual phone numbers online. Furthermore, SMSOnline continuously acquires phone numbers from over 20 countries, including Tier 1 nations like Japan, China, Taiwan, South Korea, the United States, and Germany, ensuring over 100 phone numbers are always available online. No registration or personal information submission is required for using SMSOnline.